CryptoLocker is becoming the most malicious ransomware (a virus that holds your data ransom) of 2013 since your data is forever lost without a solid backup copy or shadow copy. Here is a summary of what it does and how you can protect yourself.
What does it do to my files?
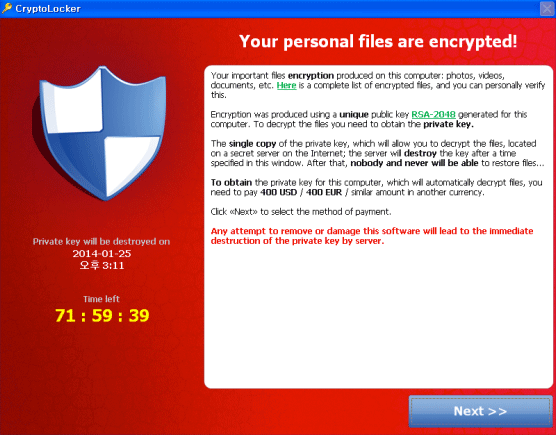
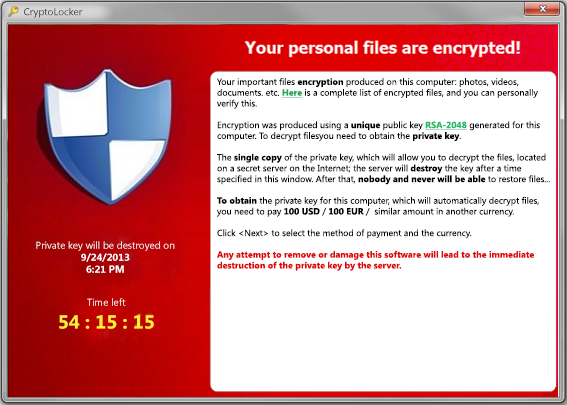
CryptoLocker will scan your computer and shared network drive for common document files and encrypt them making the files completely innaccessible until you pay a ransom of approximately $300 within 4 days. There is no way to decrypt your files even if your anti-virus cleans the infected computer.
[spoiler title=”Here is a full list of files affected:” open=”0″ style=”1″]
*.odt, *.ods, *.odp, *.odm, *.odc, *.odb, *.doc, *.docx, *.docm, *.wps, *.xls, *.xlsx, *.xlsm, *.xlsb, *.xlk, *.ppt, *.pptx, *.pptm, *.mdb, *.accdb, *.pst, *.dwg, *.dxf, *.dxg, *.wpd, *.rtf, *.wb2, *.mdf, *.dbf, *.psd, *.pdd, *.pdf, *.eps, *.ai, *.indd, *.cdr, *.jpg, *.jpe, img_*.jpg, *.dng, *.3fr, *.arw, *.srf, *.sr2, *.bay, *.crw, *.cr2, *.dcr, *.kdc, *.erf, *.mef, *.mrw, *.nef, *.nrw, *.orf, *.raf, *.raw, *.rwl, *.rw2, *.r3d, *.ptx, *.pef, *.srw, *.x3f, *.der, *.cer, *.crt, *.pem, *.pfx, *.p12, *.p7b, *.p7c[/spoiler]
How would I get infected?
CryptoLocker spreads through attachments in e-mails. The email will look like a customer support issue with a zip file attachment. The virus is inside the zip file hidden as a PDF document.
There have also been reports of people being infected by visiting a website that has Java, a common web programming language.
How can I protect myself?
There are some security policy changes that can be made to computers to prevent the virus from running, however you must be comfortable with Windows system administration to make the changes. CryptoPrevent will also make these changes for you. Although rare, you must be careful since it could disable other programs.
The most straightforward way to protect yourself now and in the future is to install MalwareBytes Pro and Avast which both detect and prevent infections. Microsoft Security Essentials is simply not advanced enough to detect this virus.
Having an office or home policy of never opening emails or attachments unless they are from a trusted sender is the first line of defence.
What are my options if I am infected?
The best way to recover from an infection is to run the free version of MalwareBytes to delete the virus, then recover your encrypted files from a backup.
Alternatively, you can use ShadowExplorer or Shadow Volume Copies to recover an older un-encrypted version of the file only if System Restore is enabled in Windows.
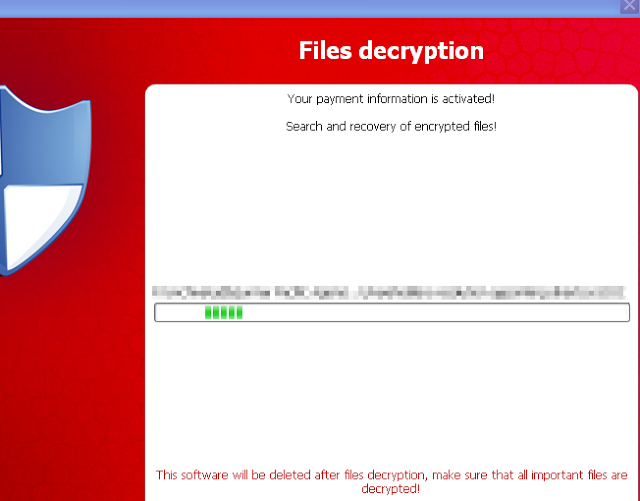
If you have no backup, your only option is to pay the ransom and wait for your files to be decrypted by the virus.