It’s irritating to find a fresh PC full of unnecessary preloaded software, but a Lenovo rootkit has been found sneaking software onto PCs after installation.
Preloaded software such as this is called ‘bloatware’ as it uses up vital system resources, but provides virtually no benefit to the user. Many users, therefore, like to perform a fresh Windows install after unpacking their system to eradicate this pesky bloatware.
Let’s take a look at how they’re achieving this and what it means for you.
Access via Rootkit?
Many people are accusing Lenovo of resorting to rootkit tactics to make sure their software remains on your system. A rootkit is a malicious piece of software which grants access to your system to remote users. This is commonly used by criminals to steal passwords or credit card details.
However, in this instance Lenovo isn’t actually using a rootkit and they’re not trying to steal your personal details.
How is Lenovo Gaining Access?
Lenovo is actually loading bloatware on to systems by taking advantage of an official piece of Windows software known as the Platform Binary Table (WPBT). The WPBT allows manufacturers to install trusted software to systems in order for them to run properly.
This software needs to be stored within the machine on a physical medium e.g. a hard drive. Now, the most obvious thing to do would be to uninstall this unwanted software, but this is where Lenovo starts to play nasty.
Built into the Lenovo system’s firmware is a piece of software known as the Lenovo Service Engine (LSE). And the LSE runs before Windows boots up and replaces Microsoft’s version of ‘autochk.exe’ with its own.
Normally, autochk.exe is used to verify the integrity of your file system, but Lenovo’s variant installs software which connects to the internet and downloads the bloatware via the WPBT.
The problem is that because the LSE runs before Windows boots up it’s almost impossible to stop this happening even when you’ve deleted the bloatware. It will simply download again thanks to the LSE!
Cleaning up Lenovo’s Bloatware
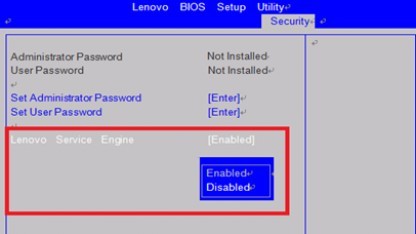
Once news of Lenovo’s shady activities came to light they were confronted with a lot of bad press.
Not surprisingly they soon released a tool to help remove this rogue software from their systems. There are also numerous guides online advising how to remove the threat manually, but this involves burrowing deep into your system’s code and is best left to an expert.
It was also revealed that all desktop machines which were built between 10/23/2014 – 04/10/2015 contained the LSE, so this is a huge number of systems which have been, to all intents and purposes, infected.
Final Thoughts
The LSE debacle has caused a lot of harm not only to Lenovo customers, but also to Lenovo’s brand values. And the ease with which the WPBT was exploited will also raise many questions about just how secure Windows is.
For more ways to secure and optimize your business technology, contact your local IT professionals.