A newly discovered ransomware called Teslacrypt is on the loose encrypting victim’s media files. Learn what it is and how to protect against it.
TeslaCrypt will lock up to 185 types of files comprising of data related to the most popular PC games played online. For instance, Assassin’s Creed, BioShock, Call of Duty, Diablo, World of Warcraft and many others are examples of games that have been affected.
The ransom
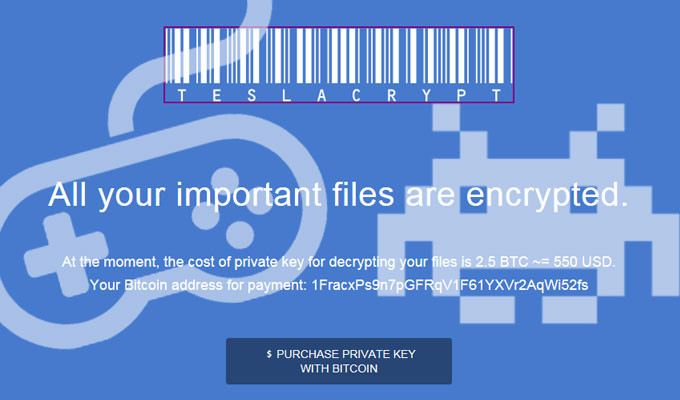
Once the files have been encrypted, the victims are prompted to pay either $1,000 through PayPal My Cash cards or $500 in Bitcoin to acquire the private encryption key to unlock their files. Criminals will prefer Bitcoin as the preferred method of payment to make them harder to track down. They’ll also use a scarcity tactic by giving those affected three days to pay the ransom.
Risk and vulnerability
According to Vadim Kotov from security firm Bromium, the vulnerability for this attack exists within Opera and Internet Explorer web browsers that visit compromised sites such as WordPress based websites. However it was Fabian Wosar from Emsisoft, an Austrian based security firm, who had discovered TeslaCrypt.
Reports show that a malicious video using Adobe Flash would play on the compromised website, which then redirects the user to a number of dodgy sites until it finally lands into its intended destination- a bundle of malware. This bundle is considered to be an exploit kit, dubbed “Angler”.
Angler plays a part towards helping computers become infected with TeslaCrypt Angler’s mission is to launch a relentless number of attacks whilst the user browses through the malicious sites with the hopes of one of them leading to its goal- to infect the system.
Once Angler gets onto a system it’ll check for two things:
- One is to verify whether the machine is a physical or a virtual one. Virtual machines are likely to be used by security firms.
- The second check detects the type of antivirus programs running alongside with the web browser.

After verifying the two checks, Angler executes attacks based on a recent Adobe Flash vulnerability (that has a patch available since last January) and a slightly older Internet Explorer exploit (security patch released in 2013). Angler preys on those who do not regularly update and patch their software, therefore it’s crucial to stay on top of updates and patch management.
What files are affected
Teslacrypt will sweep through 185 types of computer files to encrypt them. Files aren’t only limited to gaming files, it’ll also encrypt all iTunes music in .m4a format, as well as images, video, compressed files and office documents. Once those file are encrypted, they’ll change to a “.ecc” file extension.
To make things worse for unsuspecting victims, TeslaCrypt then wipes out all of the Windows restore points from the target PC to prevent restoring the files that had just been encrypted from an earlier point in time.
The three most realistic options for victims are:
- Pay the ransom, although file recovery is not guaranteed
- Run a full scan with your antivirus to remove it and then restore the locked files from a protected backup drive.
- A system reformat may be your only choice, counting your losses.
TeslaCrypt can also reach your PC through infected file attachments or a link sent through email. This includes the possibility of unsolicited private messages reaching users from social platforms such as gaming sites, which once executed, can also unravel the attack.
How to stay protected from TeslaCrypt
- Update and fully patch Adobe software and Microsoft operating systems.
- Have antivirus and antimalware running on your PC with the latest signatures to help detect Angler.
- Back up your system regularly, and when not in use, keep it offline on a disk drive separate from your PC.
- Avoid relying completely on online storage solutions such as DropBox or Box, as malware can still get to these files.
- Avoid clicking on unsolicited email messages or opening any of its contents no matter how convincing they look.
- Make use of a site advisor that’ll help block most reported sites that have been blacklisted. A good one to use is the Web Of Trust plugin for Chrome.
Zero day vulnerabilities are an ongoing cat and mouse game making it important to have security measures in place. Unaffected backups, staying up to date, and running Anti-Malware can really help save the day with ransomware such as TeslaCrypt.
For more ways to protect your business systems, contact your local IT professionals.